Overview of Integrated Windows Authentication
Integrated Windows Authentication (IWA) is a mechanism that automatically provides user authentication information to IIS when IIS and the user are logged in to the same domain. When you create a site with ASP.NET C#, you can determine whether a user has been authenticated and obtain information about authenticated users.
This allows users to access web applications hosted on (or integrated with) IIS without any additional login steps and enables SSO integration with other application servers.
*If a user is not part of the same domain or is unauthenticated and accesses the IIS page, a sign-in dialing message will be displayed. If authentication is not performed correctly, an HTTP Error 401.1 – Unauthorized will be displayed.
SSO (Single Sign On) Flow
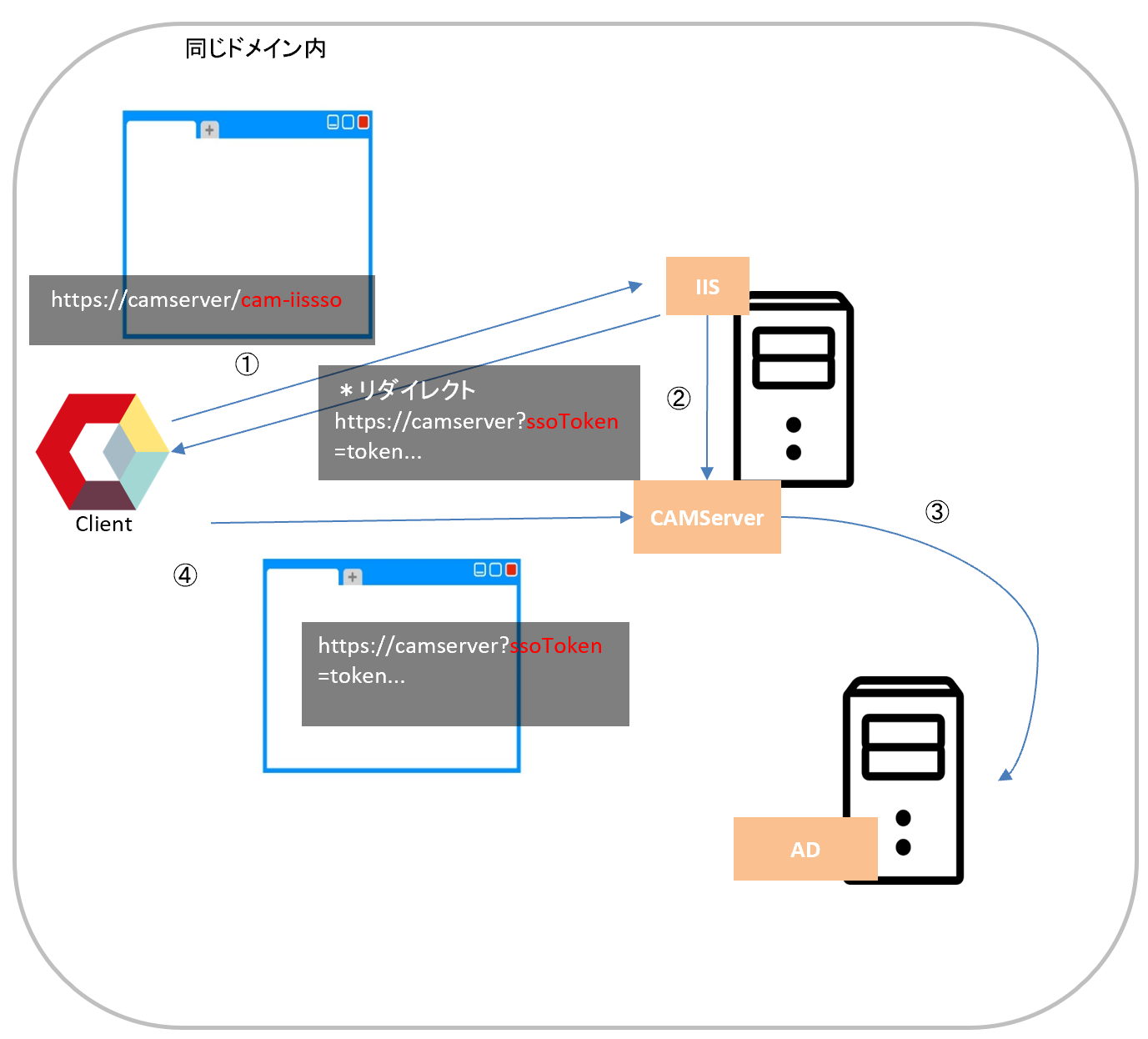
The Chat&Messenger On-Premise Ultimate plan allows SSO via Integrated Windows Authentication. The SSO flow is as follows:
- The client first accesses the Integrated Windows Authenticated page /cam-iissso.
- On the /cam-iissso page, ASP.NET determines whether the user is authenticated and connects to the CAMServer.
- The CAMServer performs an LDAP search to confirm that the user is a valid AD user, generates an ssoToken (a unique random value of 30 bytes or more) and a URL to access the CAMServer, and sends a redirect request.
- Access the CAMServer and authenticate using the ssoToken. If authentication is successful, a session ID for API access will be assigned.
Requirements for achieving SSO
Join Windows Server to Domain
Please join the Windows Server running CAMServer/IIS to the Active Directory domain.
To check the domain to which an existing Windows Server is joined, go to "Server Manager" → click "Local Server" on the left menu → click "Computer Name" and refer to the Domain column.
In addition, IIS should coexist with CAMServer on the same server and run on port 80. If you place a LoadBalancer in front of CAMServer, CAMServer will run on port 8080, so IIS can also use port 443.
Installing IIS
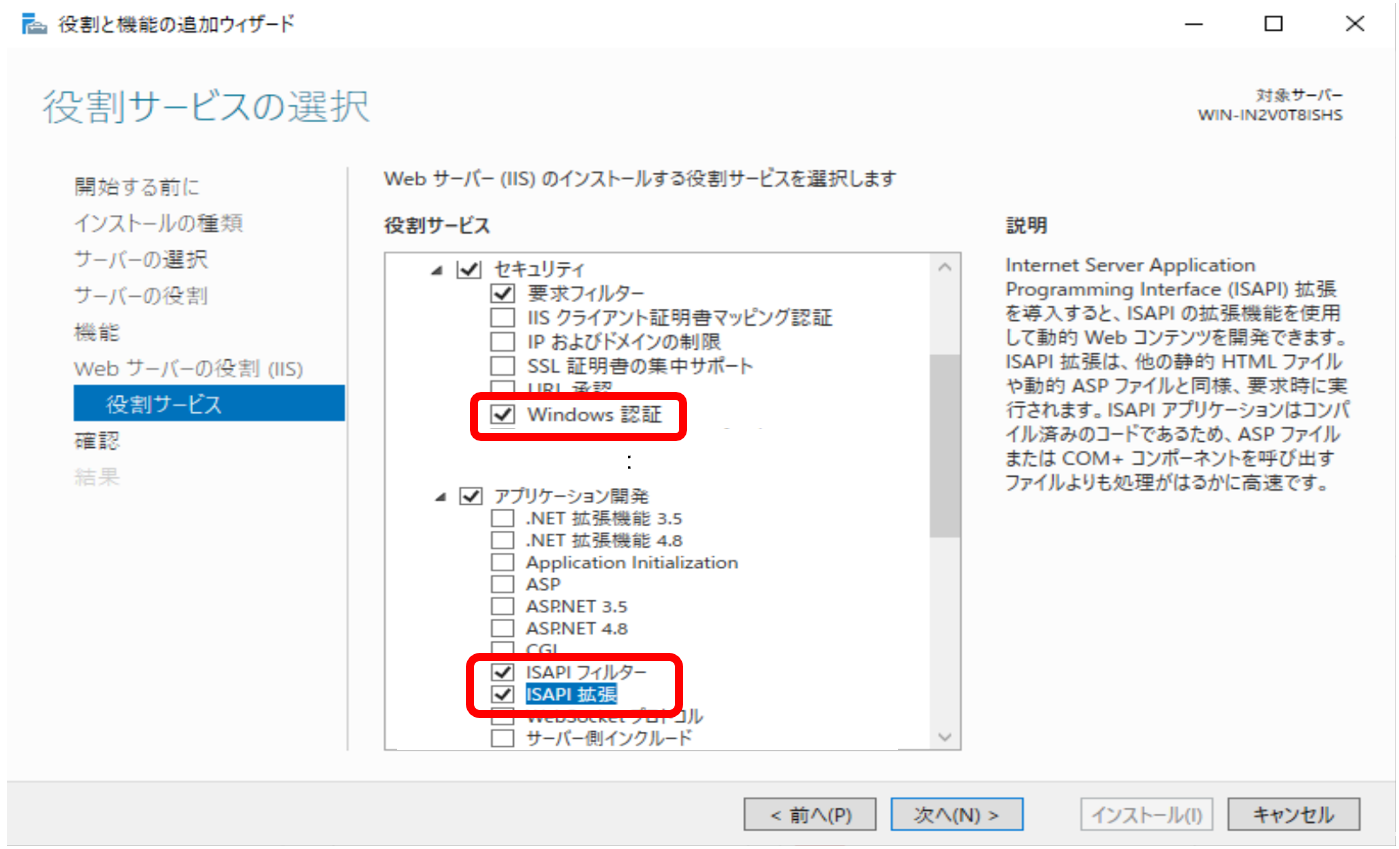
サーバの役割からIISをインストールしてください。IISインストール時に、役割サービスの選択オプションで以下チェックを行う。
- Windows Authentication
- ISAPI Filters
- ISAPI 拡張
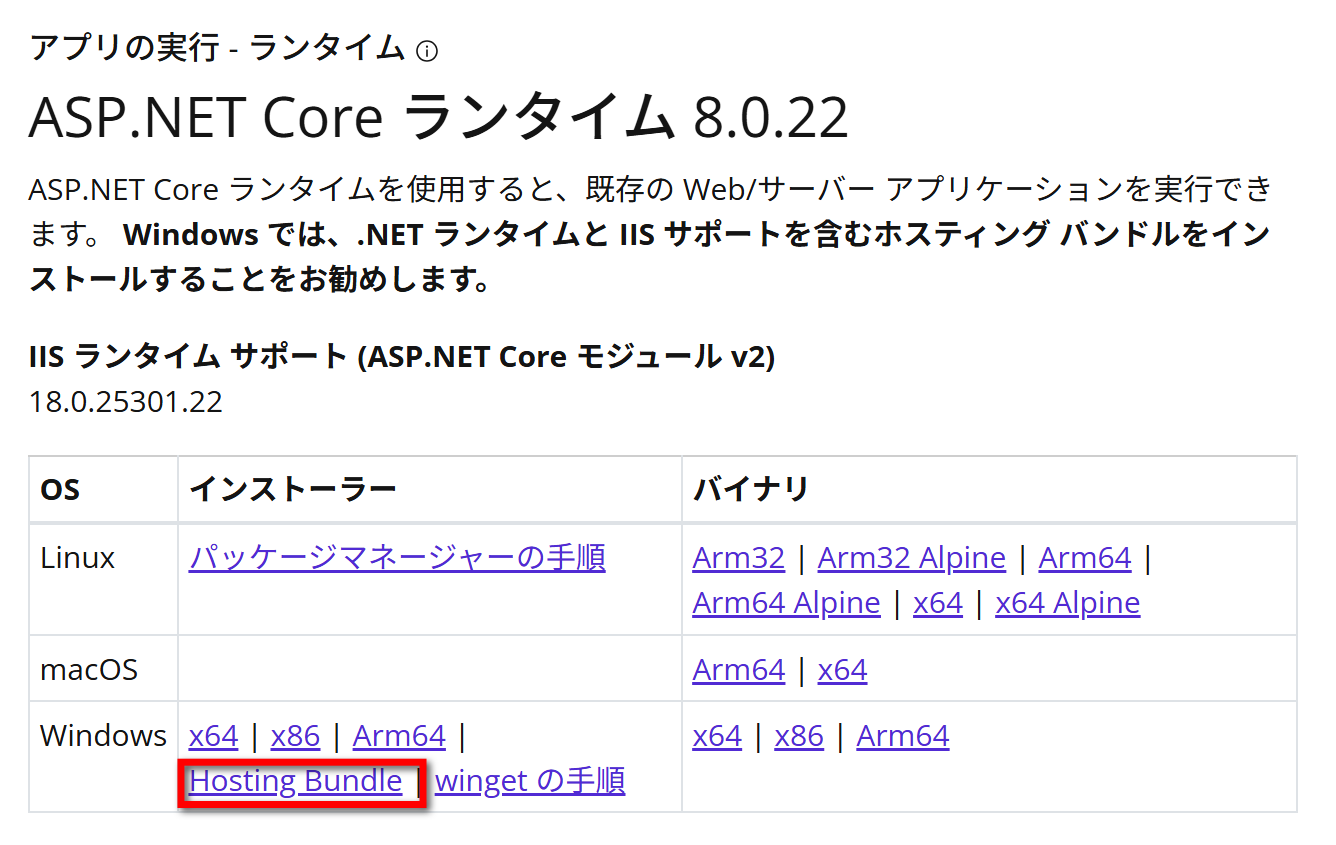
Install ASP.NET Core Hosting Bundle
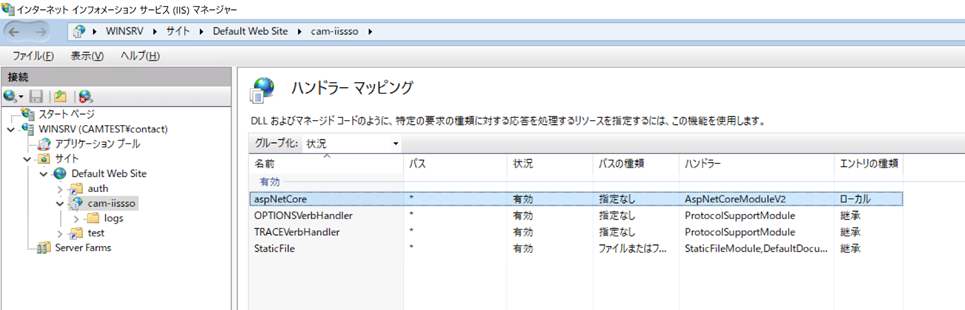
ASP.NET Core Hosting Bundle をインストールしてください。インストール後、IISを再起動してハンドラーマッピング に AspNetCoreModuleV2 が存在していることを確認してください。
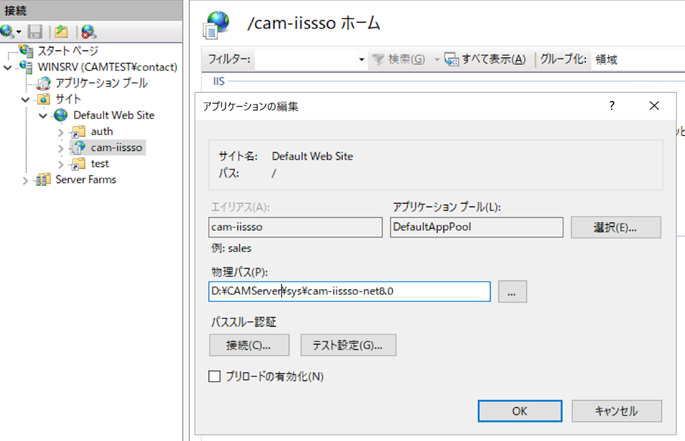
Add application (cam-iissso)
Add the cam-iissso application to the Default Web Site.
- Alias: cam-iissso
- Physical Path: \sys\cam-iissso-net8.0
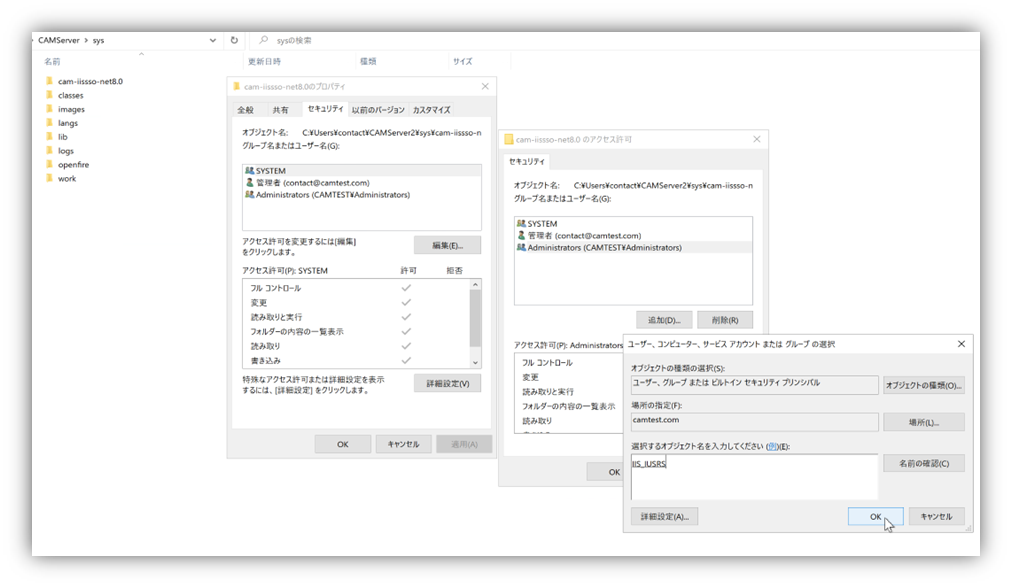
Also, grant the IIS_IUSRS group viewing permissions (Read & Execute, List Folder Contents, Read) to the cam-iissso-net8.0 folder.
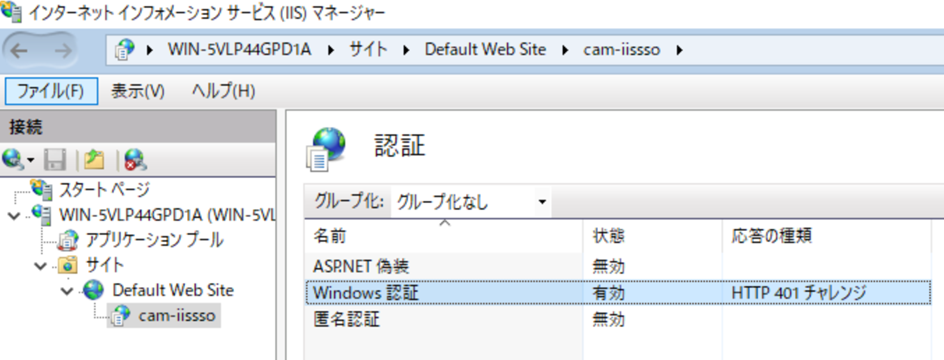
Enable Windows Authentication
Right-click "Windows Authentication" and select "Enable."
Internet Options Settings
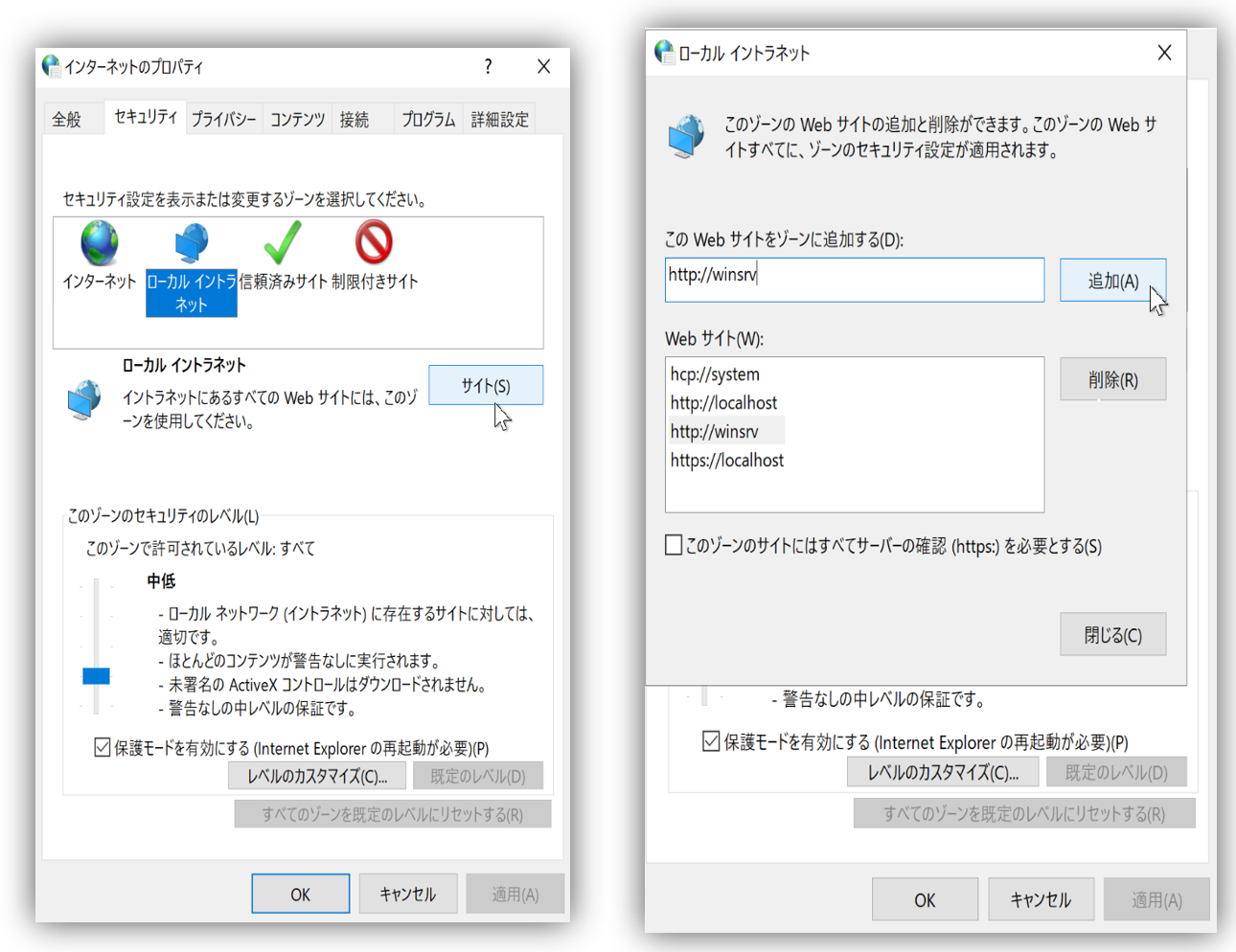
Add the site served by IIS to the Intranet Zone
Select Internet Options, click the "Security" tab, and select "Local intranet." Click the "Sites" button, select "Advanced Settings," and add the URL of the site.
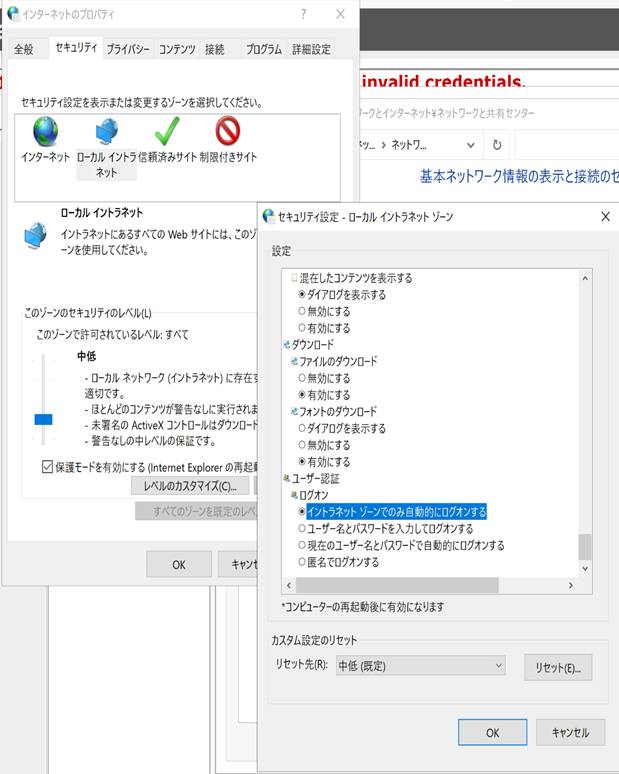
Check for automatic logon
Click "Custom Level" and make sure that "Automatic logon in Intranet zone" is selected under "User Authentication" -> "Logon".
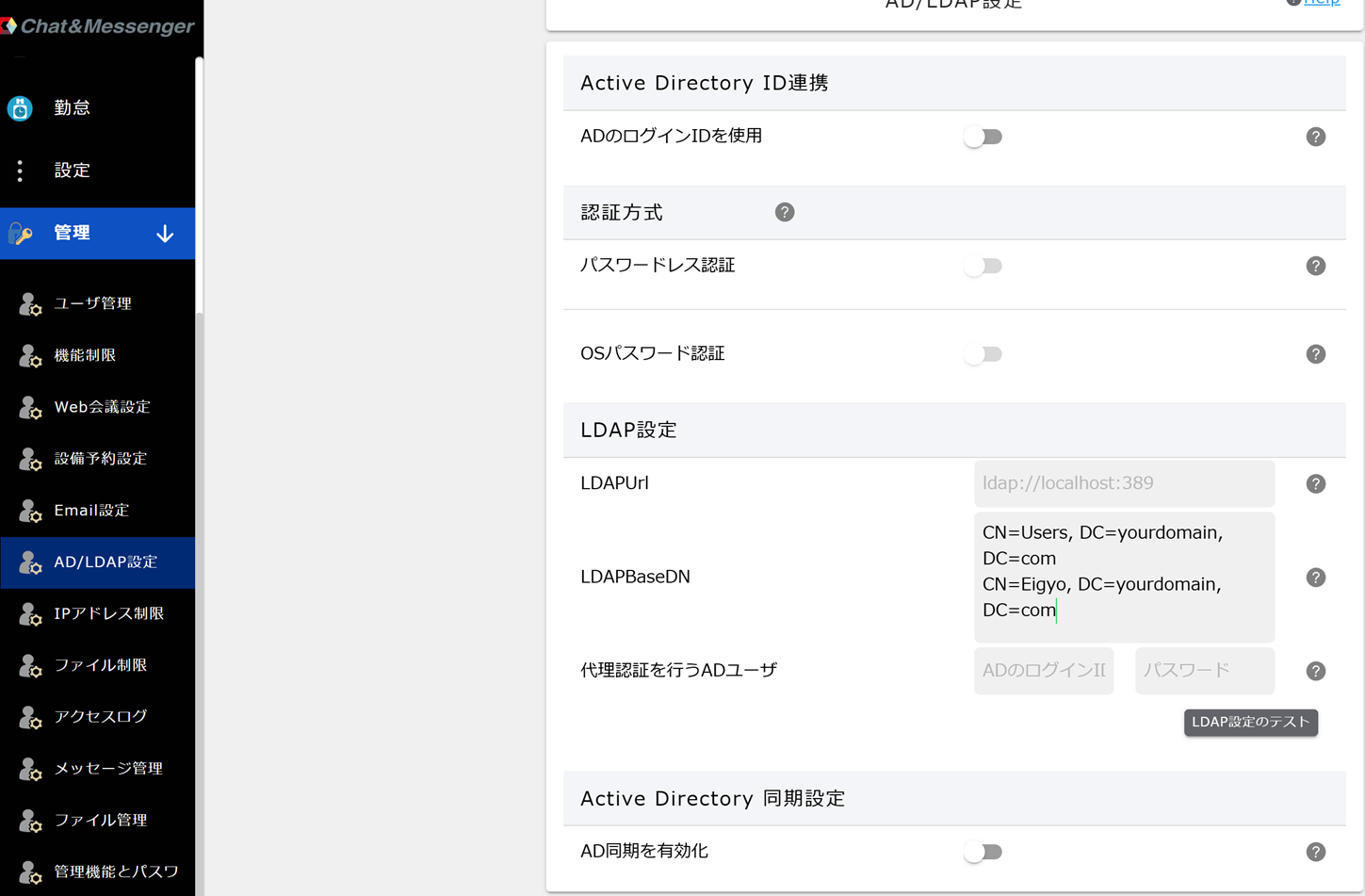
LDAP Settings
If you want to use IIS for single sign-on,LDAP Settings(LDAPUrl, LDAPBaseDN, AD user to perform proxy authentication) are required.
Access via FQDN (fully qualified domain name) and register SPN
This is not necessary if you access the IIS Windows Integrated Authentication page using a host name (NetBIOS name), but you must register an SPN if you access it using an FQDN (fully qualified domain name, e.g., sso.example.com).
SPN (Service Principal Name) is a name that uniquely identifies a specific service on Active Directory in Kerberos authentication. When accessing with FQDN, registering SPN allows the client to correctly request a Kerberos ticket for the service to be accessed.
for example https://sso.example.com When accessing, the client (browser) requests a ticket from Active Directory, saying "I want to connect to a service called HTTP/sso.example.com." Active Directory checks which account the SPN is associated with and issues the corresponding service ticket. If the SPN is not registered correctly, Kerberos authentication will fail, resulting in the display of an authentication dialog box.
The SPN registration is done on the computer account hosting IIS. For example,ad For IIS running with the host name, register the SPN as follows:
setspn -S HTTP/sso.example.com ad$Once registered, you can check with the following command:
setspn -L ad$This result HTTP/sso.example.com If it is displayed, the SPN registration was successful.
Cannot be used in HTTP proxy connection environment
Please note that SSO is not available in HTTP proxy environments.
Configuration in a LoadBalancer + SSL environment
If you are using IIS Integrated Windows Authentication in a LoadBalancer + SSL environment, please refer to the following blog article.


